We were absolutely amazed by the complete disregard for the data security over at Survival Servers, when this story broke out it appears survival servers were very late to comment on this. Based on the data available they had known about this security breach for months without informing their clients which prompts the question, how can anyone trust them with their data, let alone their game servers?
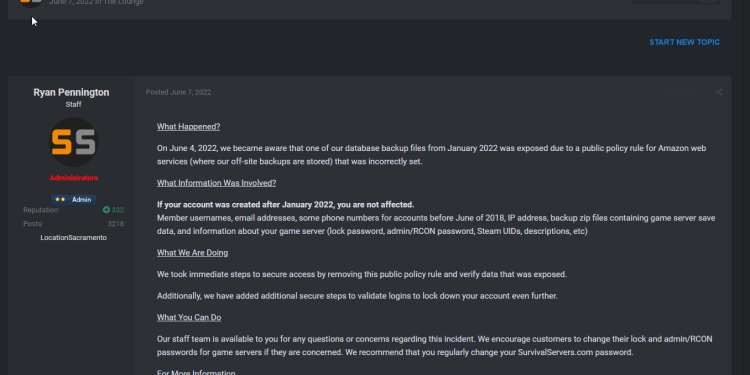
A data analysis website found the security flaw in permissions to the leaked data after months, possibly years of the data sitting there exposed, readily accessible. It was discovered that the personally identifiable information (PII) of thousands of Survival Servers users in a database backup stored improperly in a public bucket. They were publicly outed on June 7, 2022. regarding this prompting an official comment from Ryan Pennington, CEO of Survival servers on their forums.
This raises many questions, how long was the data exposed, it clearly violates many countries laws including California‘s laws on data storage and protection and given that a high percentage of clients are minors raises a huge legal and ethical question, such as breaking COPPA.
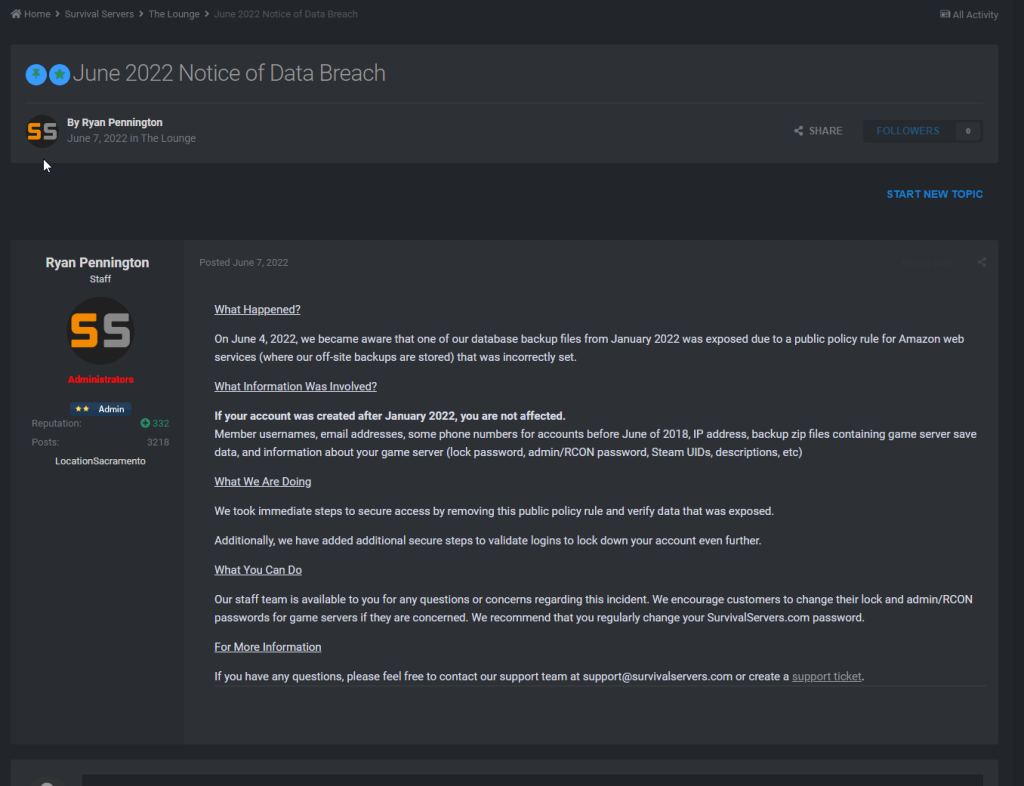
Survival Servers has confirmed that the breach affects all customers who signed up prior to February 1, 2022. The California-based company hosts and rents private gaming servers.
User Data Exposed in Database Breach
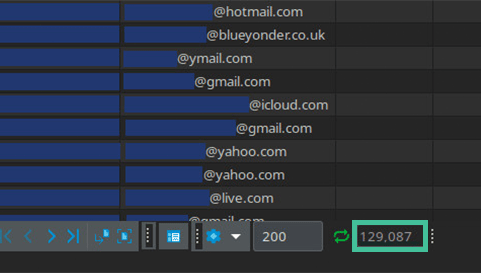
The leaked data includes the full names, email addresses, and IP addresses of 129,087 individuals. It also includes the phone numbers of some customers. The PII was stored alongside receipts of financial transactions.
“I was surprised to find several pieces of easily accessible PII information within the bucket that could be pieced together and misused by ill-intentioned individuals,” cybersecurity expert Mirza Silajdzic, who discovered the exposed data, said.
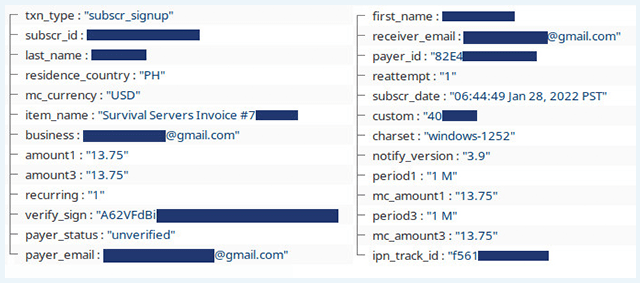
According to Survival Servers, the leak was caused by a “public policy rule for Amazon web services (where our off-site backups are stored) that was incorrectly set.”
The company said it took immediate steps to remove the database backup and secure its S3 bucket. To prevent hackers from taking advantage of the leaked data to hack its users, Survival Servers has introduced additional steps to validate users’ logins.
Steam RCON and Server Passwords Leaked
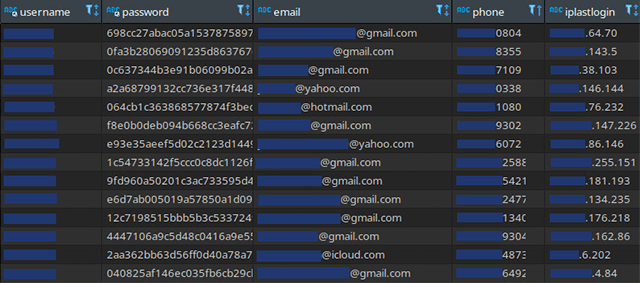
In addition to the leaked PII, our team also discovered unencrypted passwords for Steam’s remote console (RCON) service.
RCON is a protocol created by Valve for third parties to communicate with Steam’s game servers. It allows customers to control a server remotely using a web interface.
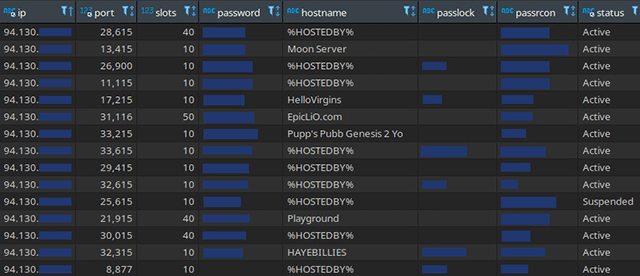
It was found that both administrative passwords and other credentials could be used to access game servers.
According to Survival Servers, the passwords can be used to join game sessions and manage servers. Survival Servers user account passwords were also exposed, but were hashed securely.
Timeline
This is a timeline of the Survival Servers breach:
| Event | Date |
|---|---|
| Independent Security Companies Discovered the database backup in an insecure bucket. | June 4th, 2022 |
| Discovered PII and details of financial transactions in the database. | June 6th, 2022 |
| Reported the breach to Survival Servers. | June 7th, 2022 |
| Breach was closed. | June 4th, 2022 |
While several security companies were investigating the breach, a popular password/data leak website haveibeenpwned.com was also conducting its own investigation. As a result, which also reported the leak. According to Survival Servers, the breach was already fixed around this time however data leaked could be used to access services which exposed further information.
Gamers’ PII Exposed
Gamers, gaming communities and gaming companies are frequently targeted by cybercriminals. We have reported on phishing, malware, and DDoS attacks targeting gaming platforms like Discord where millions of gamers congregate. The personal data we have found both in this data dump and others was easily accessible and could be pieced together by malicious individuals to commit identity fraud, access personal accounts of clients and other malicious attacks.